Policy Basics in the Azure Portal
Use a simple policy to stipulate the permitted regions for your deployed resources.
Table of Contents
Introduction
Most organizations don’t want users creating Azure resources in any region. In this lab we’ll specify that resources can only be created in the UK.
Using Policy from the portal
-
Open the Azure Portal and create a resource group called PolicyLab
-
Launch Azure Policy
You may also want to favourite it by selecting All Services, searching for Policy and clicking the star
-
Select Definitions on the left side of the Azure Policy page
Definitions are effectively the restriction you want to impose. You can use the built in policies, duplicate and edit them, or create your own from various templates like those on GitHub
-
In the search text box, type “location” and open up the “Allowed Locations” definition
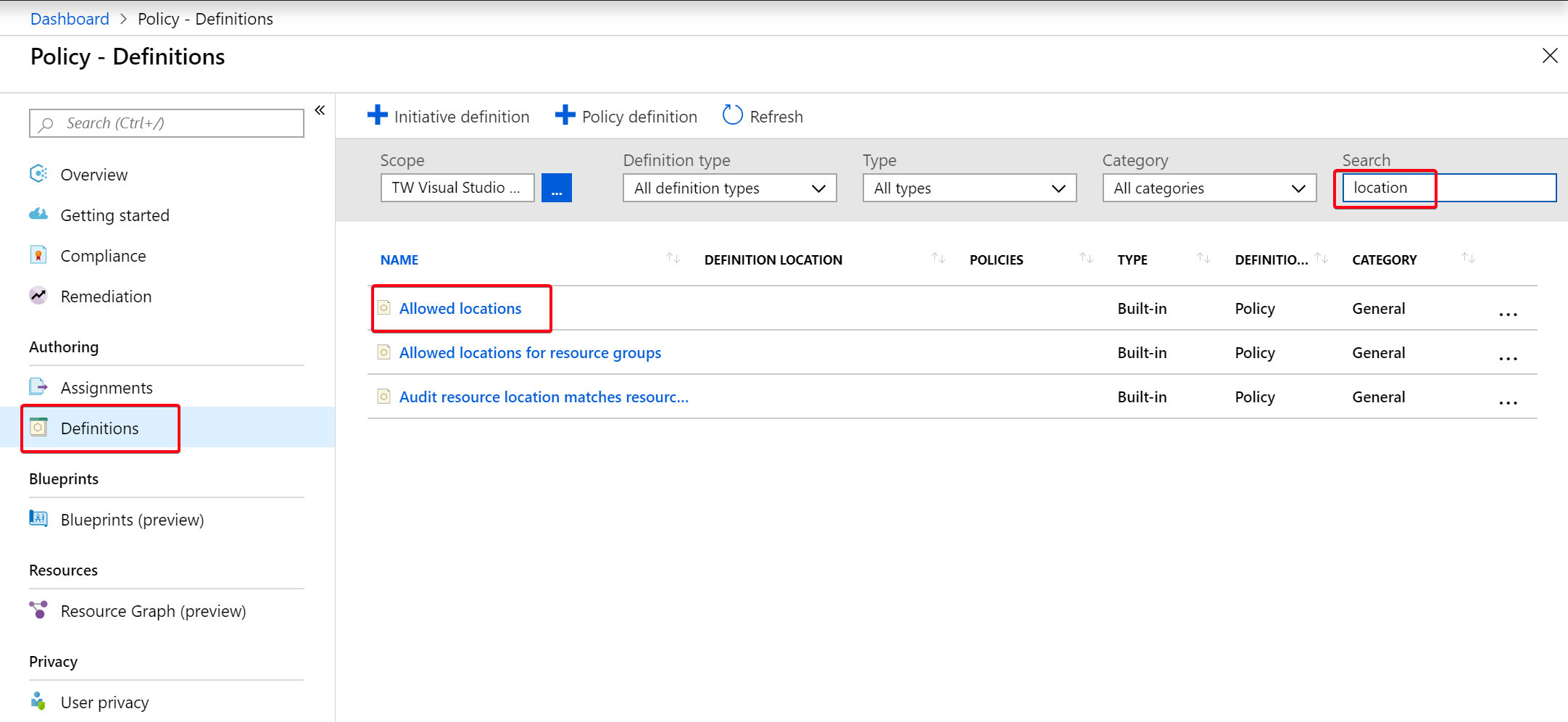 Figure 1: Policy Definition
Figure 1: Policy DefinitionYou can see the definition is a JSON file that needs a list of allowed locations and will cause a deny. You could duplicate this definition and add more checks if needed but we’ll just assign it.
-
Clicking Assign
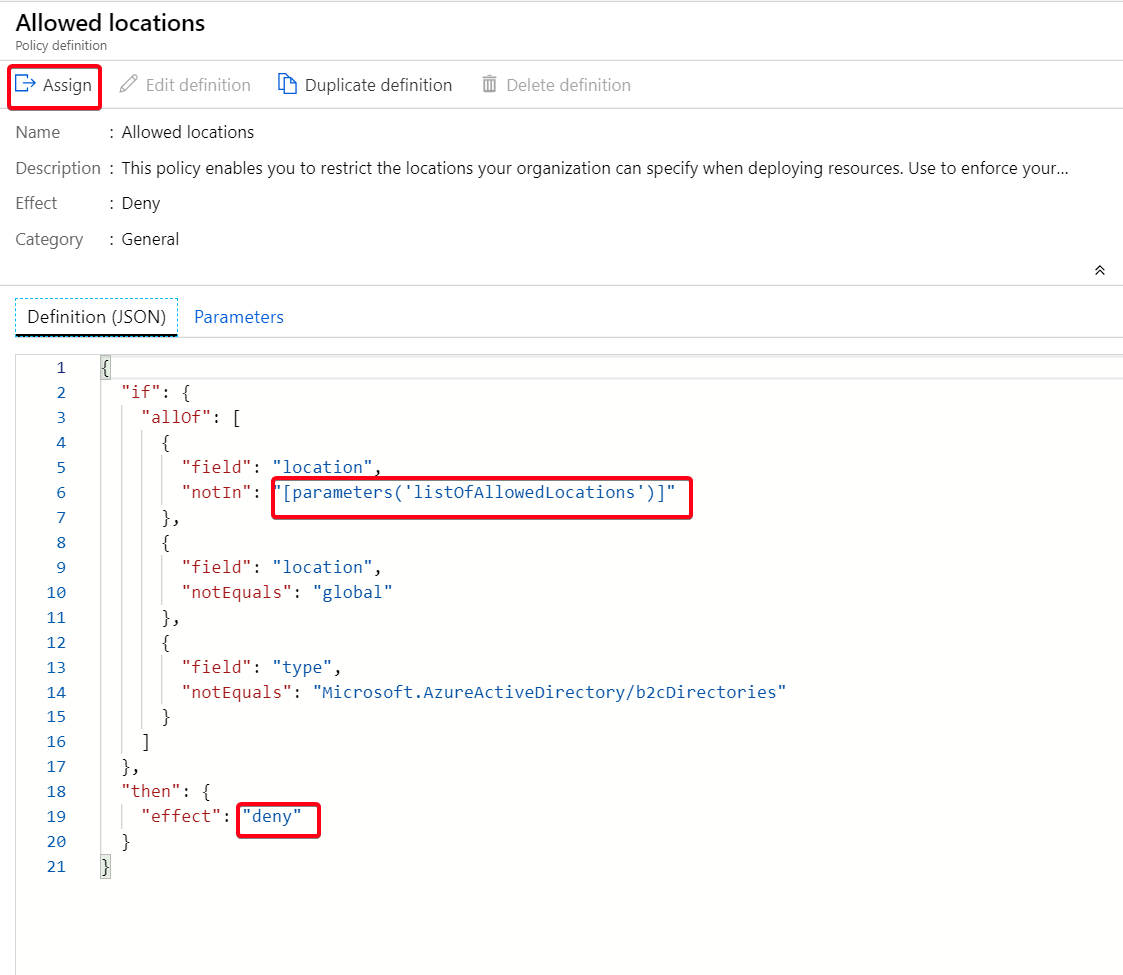 Figure 2: Policy Definition - Allowed Locations
Figure 2: Policy Definition - Allowed LocationsFor more details on the policy definition structure see here.
-
When assigning a policy, we first have to choose the scope, at either:
- Management Group
- Subscription
- Resource Group
You can think of management groups as a folder hierarchy where subscriptions can be organised.
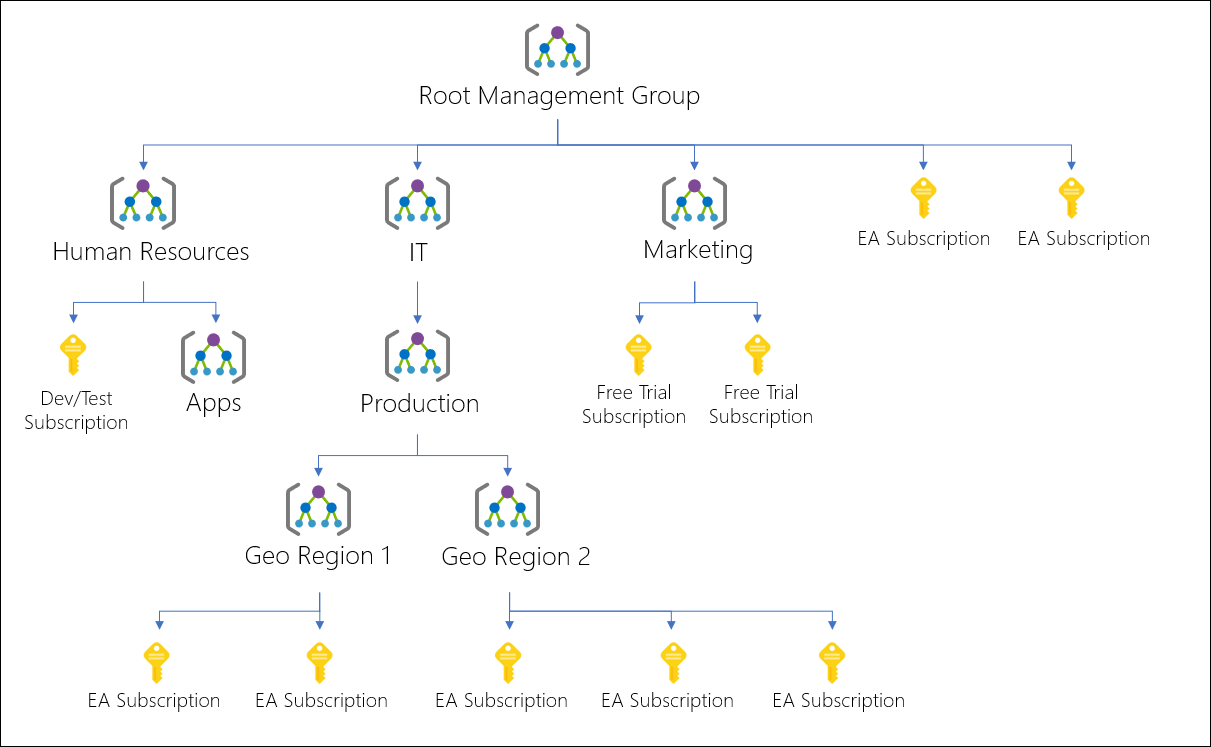 Figure 3: Management Group
Figure 3: Management GroupThe scope chosen will take effect on all child resources below it, but you can add exclusions if needed.
-
In the Basics section you can change the assignment name and add a description
Description are definitely recommended when you have a lot of policies.
-
In the Parameters section choose the allowed locations of UK South and UK West
As this is a Deny policy there is no need for Managed Identity and we’ll get in to that in a later lab.
-
Click Assign.
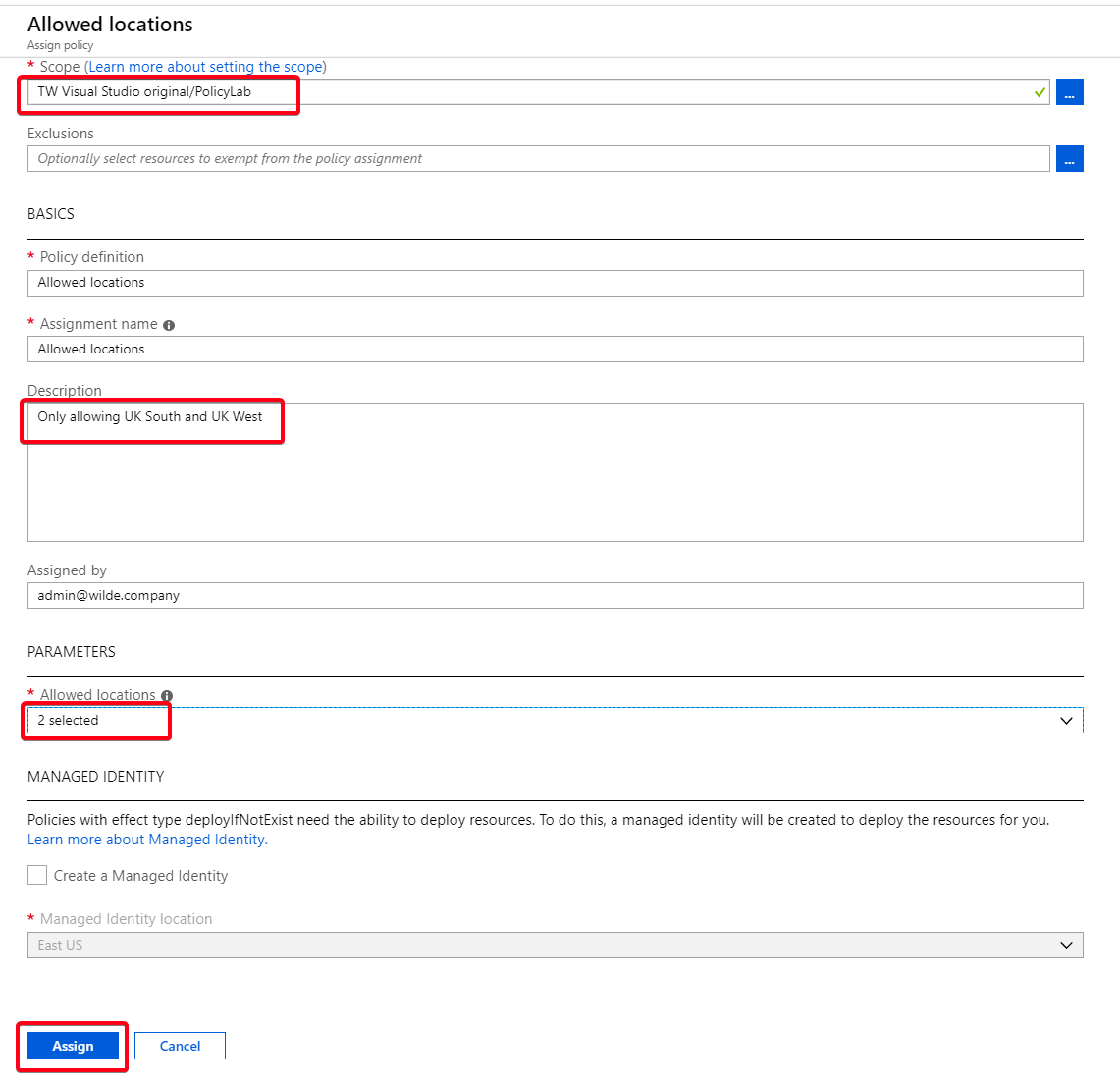 Figure 4: Assigning Allowed Locations Definition
Figure 4: Assigning Allowed Locations Definition
Testing the Deny policy
-
Now test creating a resource in the PolicyLab resource group with a location outside the UK
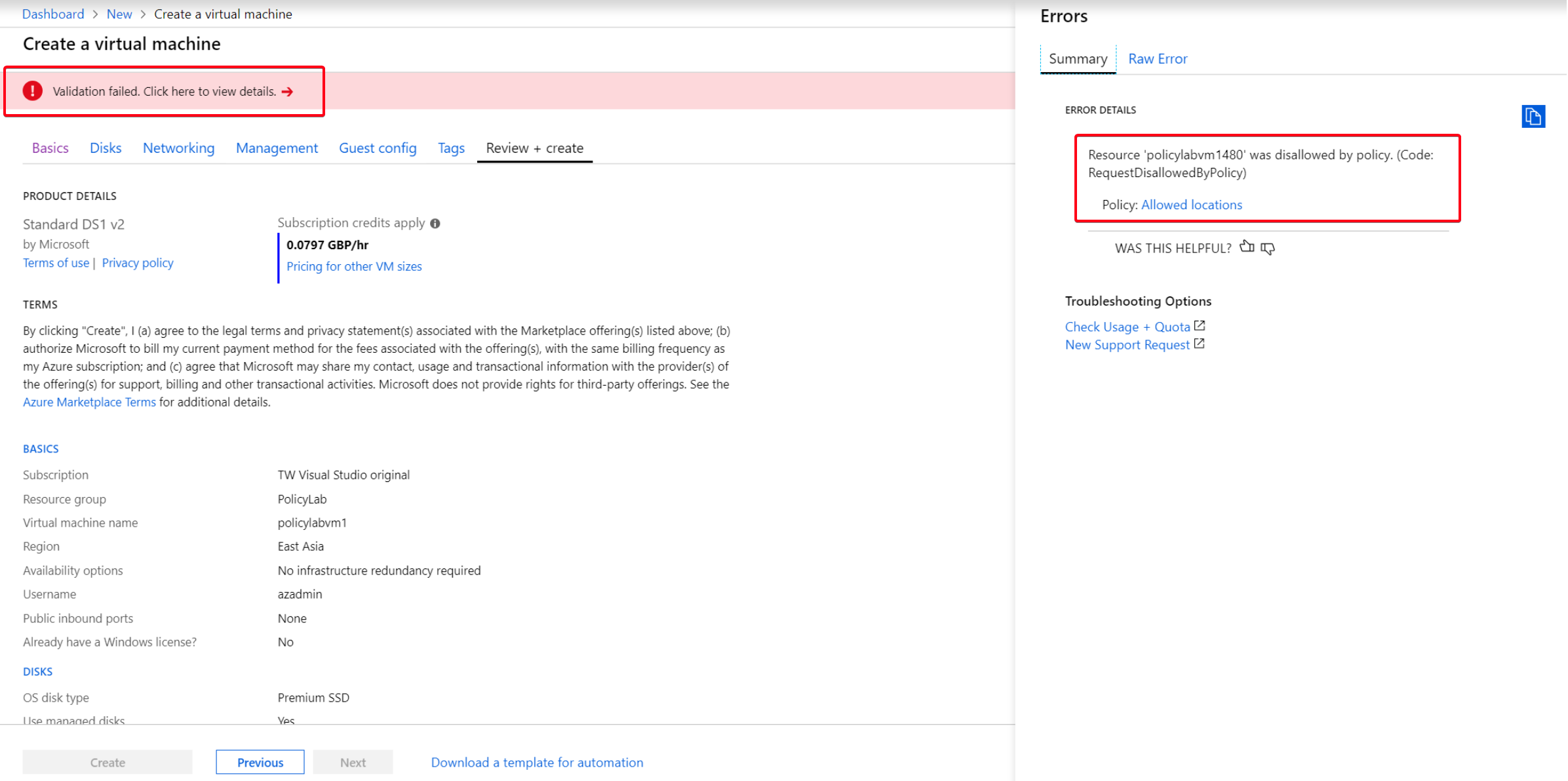 Figure 5: VM deployment failure to non-UK location
Figure 5: VM deployment failure to non-UK location -
Now test creating a resource in the PolicyLab resource group with a location inside the UK and the resource should be deployed as normal
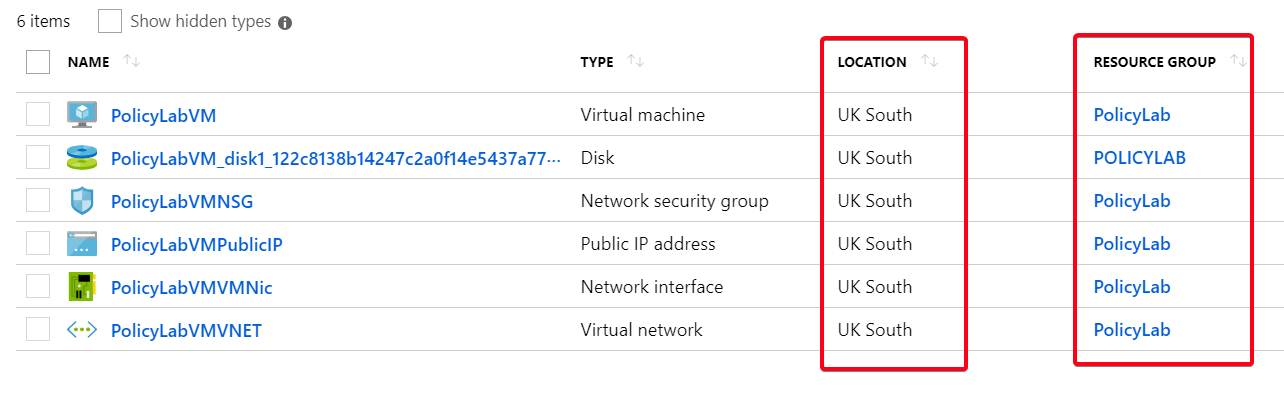 Figure 7: VM deployment success to UK location
Figure 7: VM deployment success to UK location
Finishing up
That concludes this lab, where we’ve learnt about applying a policy from the Azure portal. The resources you’ve created will be used in the next lab so don’t delete them yet.
Next we’ll tackle another common requirement, specifying which VM SKUs are allowed to be deployed. We’ll start to automate policy creation too.