GitHub Copilot CLI and WorkIQ
Table of Contents
How do you add Work IQ as an MCP server if your GitHub Copilot CLI is running in WSL2? Here is an option that was shared with me when I hit into a security policy at work. I thought I’d pass it forward.
Adding MCP tools into GitHub Copilot gives an amazing extensibility and also allow Copilot’s various models to reason across context from multiple sources. In the last blog I added the Microsoft Learn MCP server to GitHub Copilot (GHCP) which I run in Ubuntu in WSL2.
Microsoft’s three IQ products were announced at Ignite back in November and extend Microsoft 365 Copilot with greater context:
- Work IQ provides insights into you, your organisation, people you work with, and your work
- Fabric IQ enables analytics and business intelligence across the data estate and its ontology
- Foundry IQ offers amazing agentic RAG grounding with defined knowledge bases and extended knowledge source support
We’ll see lots of use cases with agentic AI leveraging these - and often together - but I thought I’d start simple and bring my work context into my conversations with GitHub Copilot.
WSL2 Issue
After following the official Work IQ MCP preview instructions it all looked good, but I then came up against a security policy issue that prevented me from using it. Work IQ was permitted on enrolled devices, and WSL2’s subsystem does not show up that way.
Workaround
The answer is to reconfigure the MCP server to run at the Windows OS level, rather than natively in the WSL2 subsystem. THis is easy as WSL2 supports running Windows commands directly within the subsystem.
Here’s how to configure it.
Installing Work IQ at the Windows OS level
Open PowerShell as admin. (I right click on the Windows icon, select Terminal (Admin), and then open PowerShell 7.)
-
Install NodeJS if you don’t have it.
winget install OpenJS.NodeJS.LTS -
Find the most recent tarball for Work IQ
npm view @microsoft/workiq dist.tarballExample outputhttps://registry.npmjs.org/@microsoft/workiq/-/workiq-0.2.8.tgzOr run the command without dist.tarball to get detailed release info (from
npm help view).npm view @microsoft/workiqExample output@microsoft/workiq@0.2.8 | SEE EULA | deps: none | versions: 4 MCP server for Microsoft 365 Copilot https://github.com/microsoft/work-iq-mcp#readme keywords: copilot, m365, mcp, mcp-server, ai, agents, workiq bin: workiq dist .tarball: https://registry.npmjs.org/@microsoft/workiq/-/workiq-0.2.8.tgz .shasum: f1b934c506994cde6c87a94e00349f792d105ff7 .integrity: sha512-pbgnJDLPGrsYb5mCY6WzFtUNcRwSHkll7phgx+DZXSDbZoPs6mDJtQ2s39606Rp8qpx7b3OrkfFOr0SuzPIVEA== .unpackedSize: 119.0 MB maintainers: - microsoft1es <npmjs@microsoft.com> - microsoft-oss-releases <microsoft-oss-publishing@microsoft.com> dist-tags: latest: 0.2.8 published 2 weeks ago by microsoft1es <npmjs@microsoft.com>
-
Install Work IQ globally
npm.cmd install -g https://registry.npmjs.org/@microsoft/workiq/-/workiq-0.2.8.tgz -
Close down and then reopen PowerShell
-
Accept the EULA
workiq.cmd accept-eula -
Test it out
workiq.cmd ask --question "Who is my manager?"
Reconfiguring Work IQ in WSL2
-
Open GitHub Copilot CLI
copilot -
Remove the workiq plugin
The default commands install Work IQ as a plugin using npx. If you have it and need too remove it:
/plugin uninstall workiq -
Add in the WorkIQ MCP server
/mcp add WorkIQThis will open up the interactive MCP addition and the name will have been prepopulated.
-
Leave the Server Type as Local.
-
Set the Command
powershell.exe -c "workiq.cmd mcp"
Leave the other fields as default and save with ctrl+s.
-
-
Display the MCP server
/mcp show WorkIQExample Output● MCP Server: WorkIQ Type: local Command: powershell.exe Status: Enabled Tools (2/2 enabled): ✓ accept_eula: Accept the End User License Agreement (EULA) to enable full ... ✓ ask_work_iq: Ask a question to Microsoft 365 Copilot for information abou... -
Display as JSON
You can run shell commands within GutHub Copilot CLI by either prefixing them with
!or by using *shift+tab. Either way will switch you into the yellow Shell mode.jq < ~/.copilot/mcp-config.jsonExample mcp-config.json{ "mcpServers": { "MicrosoftLearn": { "tools": [ "*" ], "type": "http", "url": "https://learn.microsoft.com/api/mcp", "headers": {} }, "WorkIQ": { "type": "local", "command": "powershell.exe", "tools": [ "*" ], "args": [ "-c", "workiq.cmd mcp" ] } } }
Work IQ in use
Now that Work IQ is configured as an MCP server, you can ask GitHub Copilot CLI questions about your work context and it will use the WorkIQ MCP to query your Microsoft 365 data.
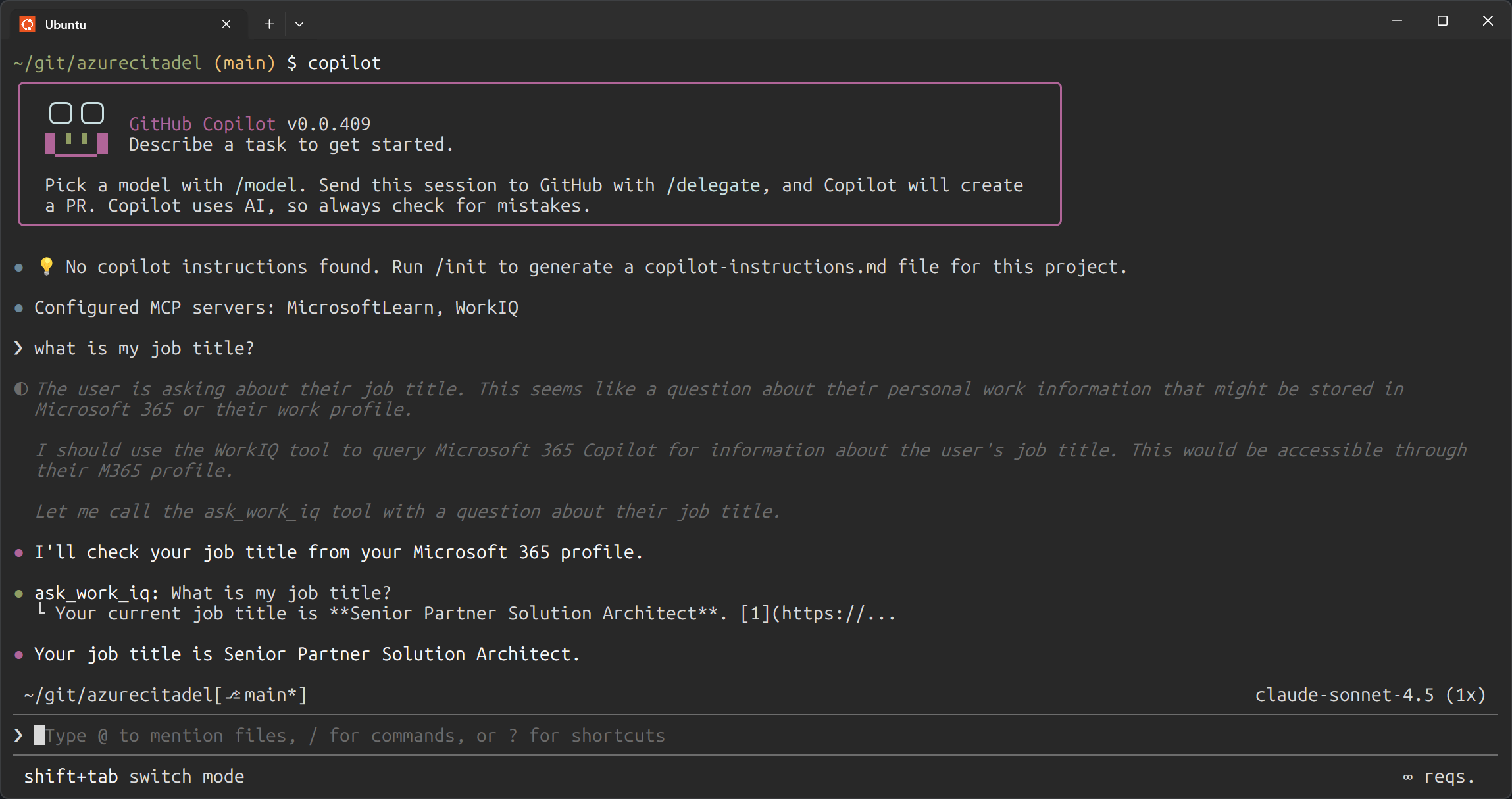
This demonstrates the power of combining GitHub Copilot CLI with Work IQ - you can now ask questions about your work context and get answers directly within your development workflow.