Monitoring
Configure the new Azure Monitor agent and Data Collection Rules. Optionally integrate with 'Microsoft Defender for Cloud' and Azure Sentinel.
Table of Contents
Introduction
Azure Monitoring agent (AMA) is the next version of the monitoring agent deployed to guest operating systems and is now generally available.
In time it will replace the older monitoring agents known as the Log Analytics Agent (MMA), Diagnostics and Telegraf agent, but there are currently some gaps so it is common to install multiple agents to achieve the required functionality. The Azure Monitor agents overview details the current situation and is updated regularly as functionality is migrated over.
In this challenge, we will deploy the new agent. After the onboarding process, we will then utilise the new functionality of this agent.
Azure Monitor Agent (AMA)
-
Confirm the Azure Monitoring Agent is on our virtual machines via the Extensions pane
-
Confirm the virtual machine’s AMA agents are communicating to an Azure Monitor workspace
Hint: query for the heartbeat
Note that you will be using CLI commands to install the agent rather than the portal or by using Azure Policy. There are Azure Policy and Initiative definitions to install the Azure Monitor Agent, but they do not currently cover Azure Arc VMs. Expect that to change soon.
Data Collection Rules (DCRs)
DCR Overview
One of the benefits of the AMA agent is the flexibility in data collection rules, which allow you to define which metrics or logs you want to send to which target, and then associate with different groups of servers including hybrid servers. Some of the policy initiatives will assign an identity, install the extension and associate with a DCR.
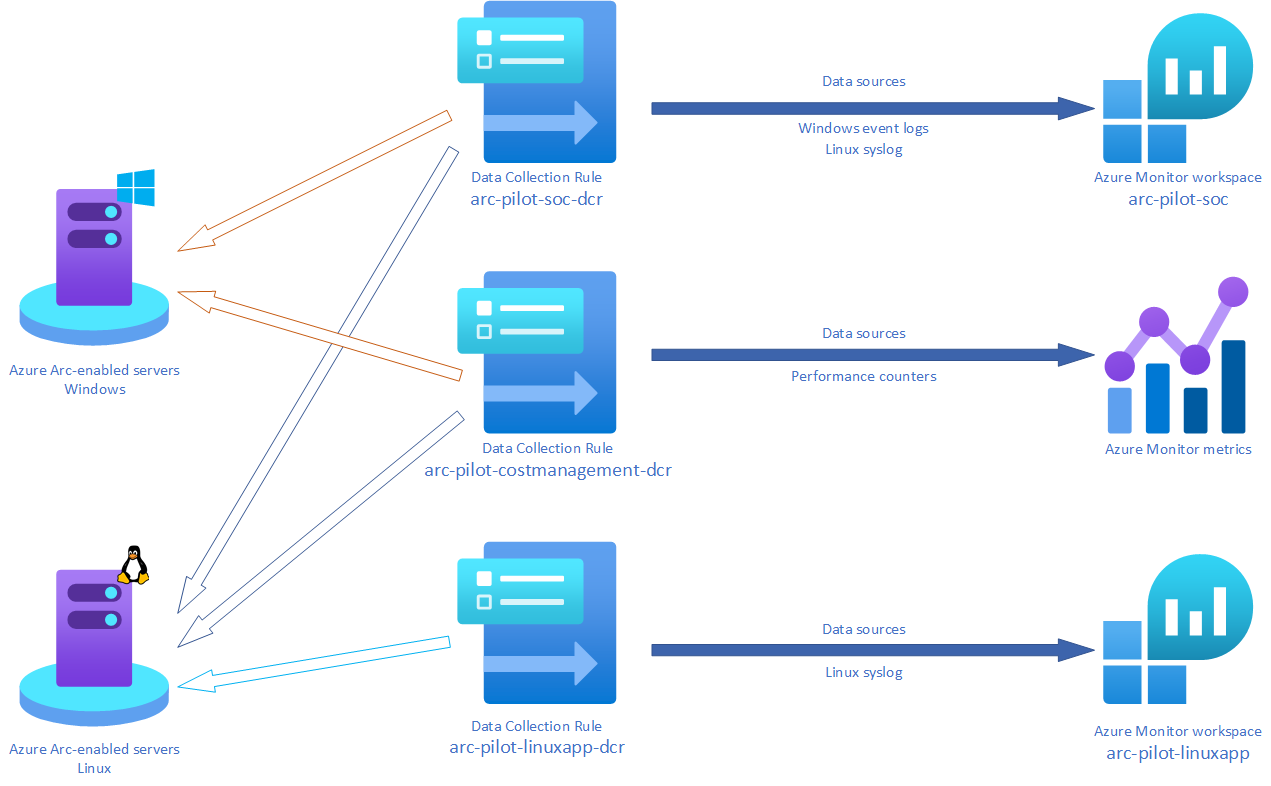
Here is an overview of the metric and log collection designed for the pilot.
Security Operations Centers (SOC) team
You are part of the Security Operations Centers (SOC) team. You have access to the arc-pilot-soc
-
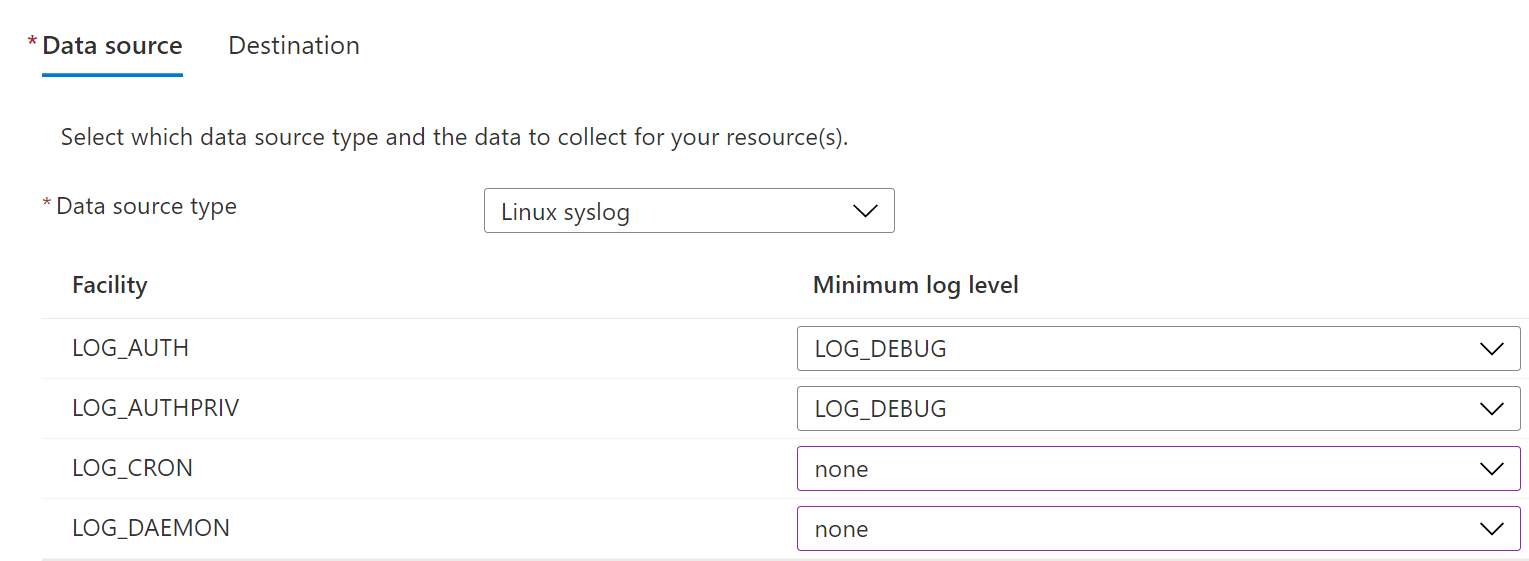
Set up a Data Collection Rule for all your Azure arc virtual machines to send their security logs to
-
(Optional) Validate the security logs are visible in the Log Analytics Workspace
Hint: The linux security logs are:
Cost Management team
You are part of the Cost Management team and performing an exercise on reducing costs.
- Deploy a Data Collection Rule to collate the RAM usage data and % of free disk space for all VMs
- (Optional) Produce a workbook showing the % utilisation of CPU, RAM and free disk space for all VMs
Linux Application Team
You are part of a Linux application team.
- (Optional) Deploy a Data Collection Rule to collate any system errors and send to a Log Analytics Workspace
- (Optional) Create an Azure Monitor Alert to notify the application team on an error
Dashboarding
As you go through this section, note the queries you use.
Log Management
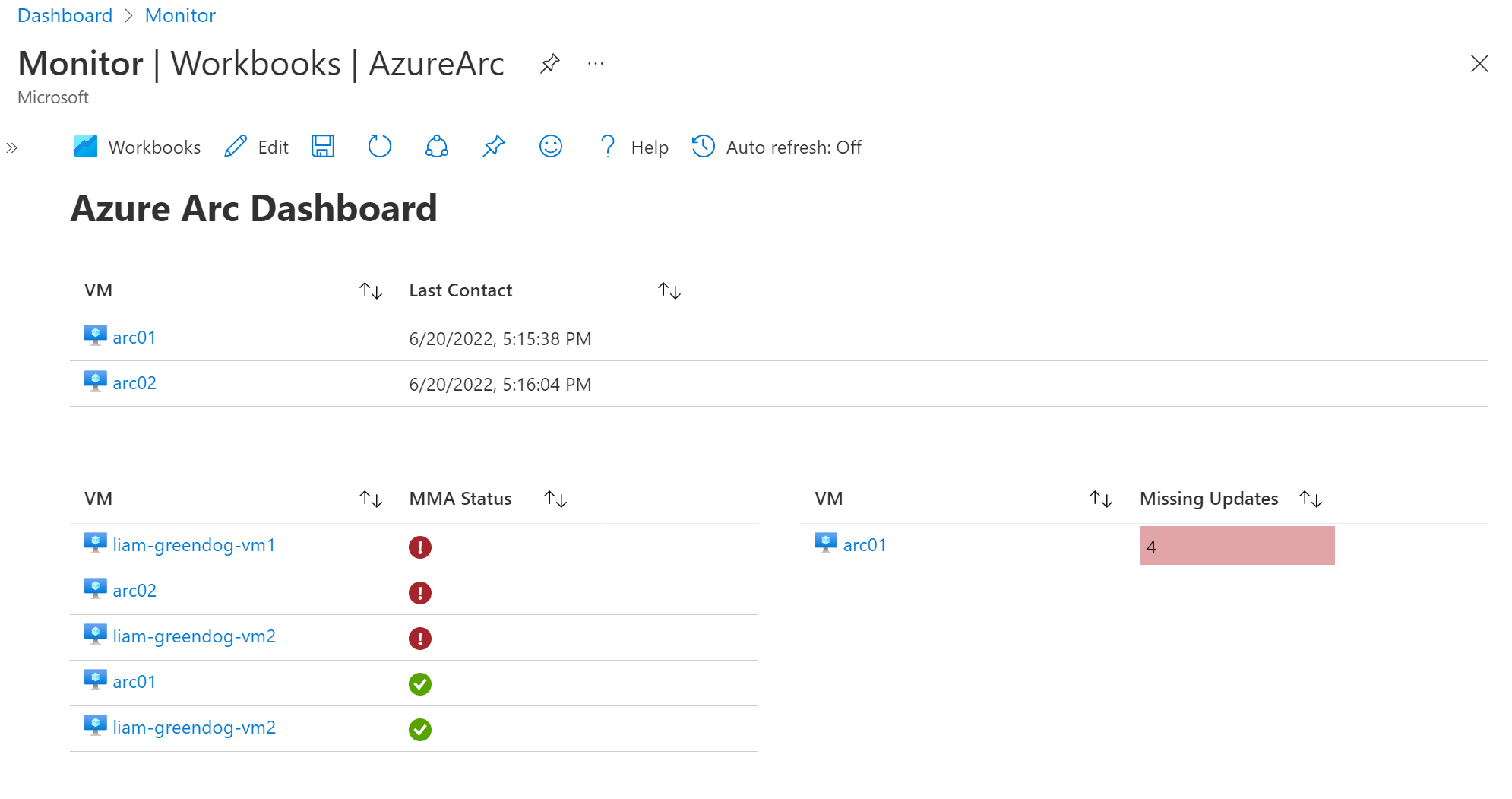
Produce a query to highlight which machines are reporting to the Log Analytics Workspace.
Update Management
Produce a query to highlight which machines require updates. (N.B. you will need to use summarize and arg_max)
Arc Management
Produce a query highlighting if our estate is compliant with the Virtual Machine extensions. (N.B. you will need to use Azure Resource Graph)
Azure Monitor Workbook
Create an Azure Monitor Workbook showcasing your KQL queries. Feel free to use graphs or charts.
Integrate with Microsoft Defender for Cloud (optional)
- Enable ‘Microsoft Defender for Cloud’ on your Azure Arc connected machines
Integrate with Azure Sentinel (optional)
- Enable Azure Sentinel on your Azure Arc connected machines by configuring the Log Analytics agent to forward events to Azure Sentinel such as Common Event Format (CEF) or Syslog
Success criteria
Screen share with your proctor to show that you achieved:
- Azure Monitor Agent (AMA) is reporting heartbeat to your Log Analytics workspace
- Data Collection Rules are defined and associated correctly with the resources
- Data is being gathered from the Azure Arc-enabled machines
Optional:
- Open ‘Microsoft Defender for Cloud’ and view the Secure Score for your Azure arc connected machine
- From Azure Sentinel, view collected events from your Azure Arc connected machine
Resources
- Azure Monitoring Agent
- Data Collection Rule
- Azure Monitor Workbook Visualizations
- Create, view, and manage log alerts using Azure Monitor
- Connect your non-Azure machines to Security Center