Azure Monitoring Agent
Summary of the switch from legacy agents (MMA, Dependency) to the Azure Monitor Agent. Enable VM Insights with the AMA.
Table of Contents
Introduction
The Azure Monitor Agent (AMA) is replacing the legacy monitoring agents.
Historically the agent based collection has been done using the Log Analytics Agent (also known as the Microsoft Monitoring Agent (MMA) agent or OMS agent), as well as the secondary Telegraf agent used for Linux metrics. It also changes how the Dependency agent is configured for Service Map information.
The older agent will be retired on August 31, 2024.
Wide World Importers have decided to exclusively use the newer AMA agent in the POC.
As a starting point, they would like to have VM Insights configured for the hybrid servers. There is a level of confusion whilst some of the documentation pages and policy definitions continue to refer to the legacy agents. However, enabling VM Insights using the Azure Monitor Agent is in preview and that is what will be configured in the POC.
Delete policy assignments
OK, first things first. We will delete a couple of the legacy policy assignments created by Azure Landing Zones.
The default policy assignments continue to deploy the legacy agents whilst some of the Azure Monitor Agent policies remain in preview. Unassign them.
-
Navigate to the Policy | Assignments blade
-
Search on Enable Azure Monitor
-
Select one of the assignments
-
Click on View definition
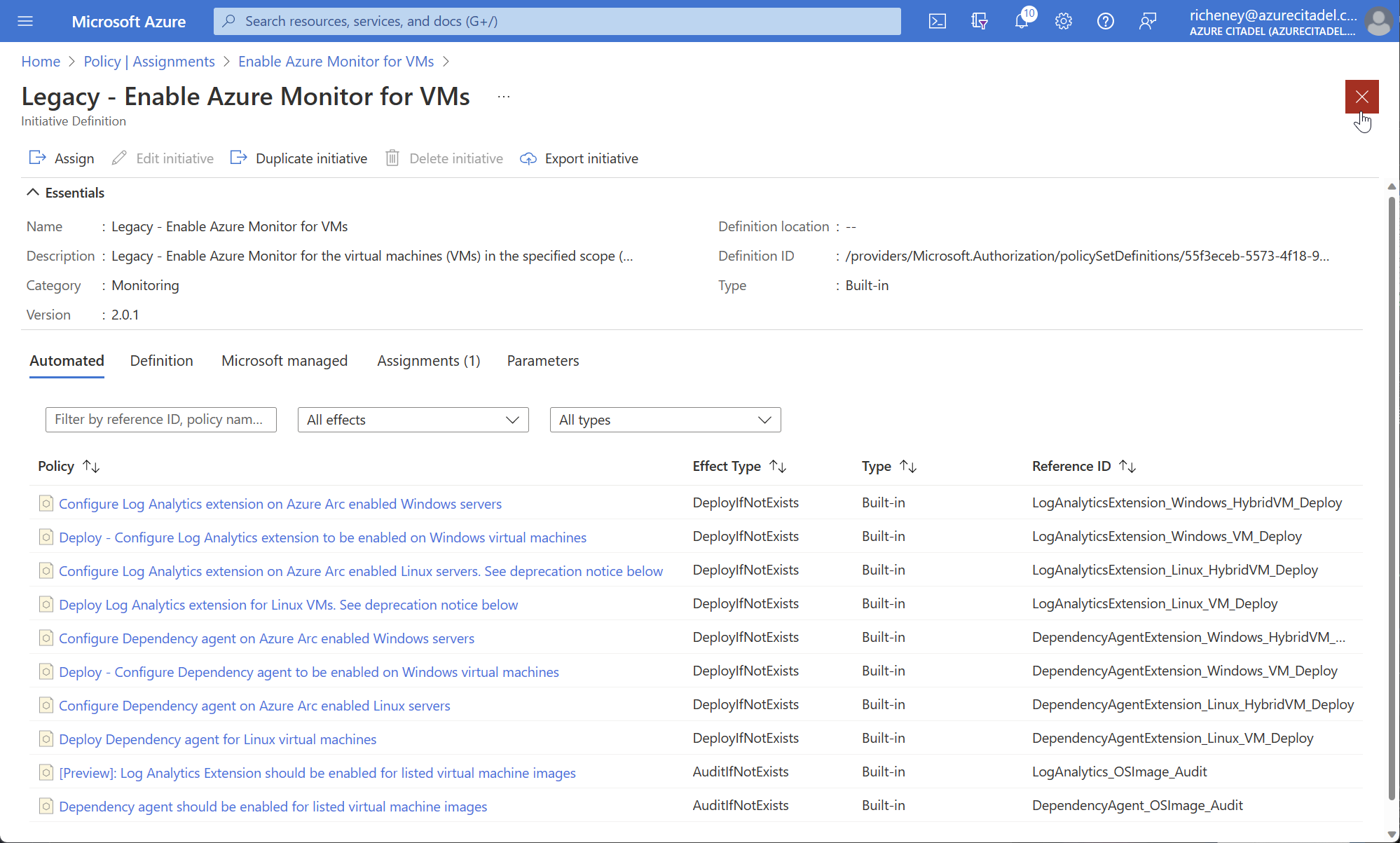
The name and description are now prefixed with “Legacy”.
-
Click on the red cross at the top right twice to return back to the filtered list
-
Delete both assignments
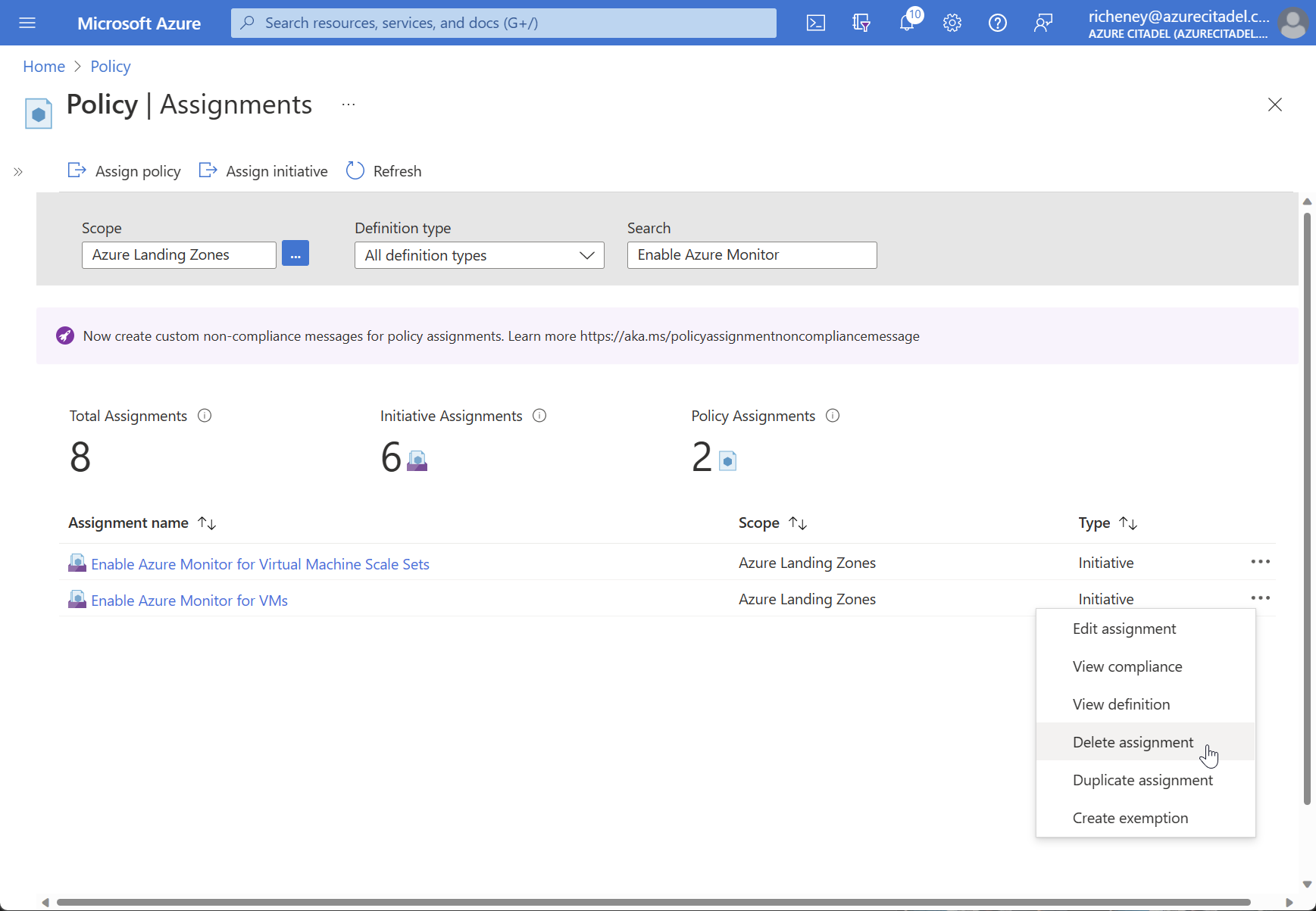
VM Insights policy initiative
-
View the Enable Azure Monitor for Hybrid VMs with AMA policy initiative definition
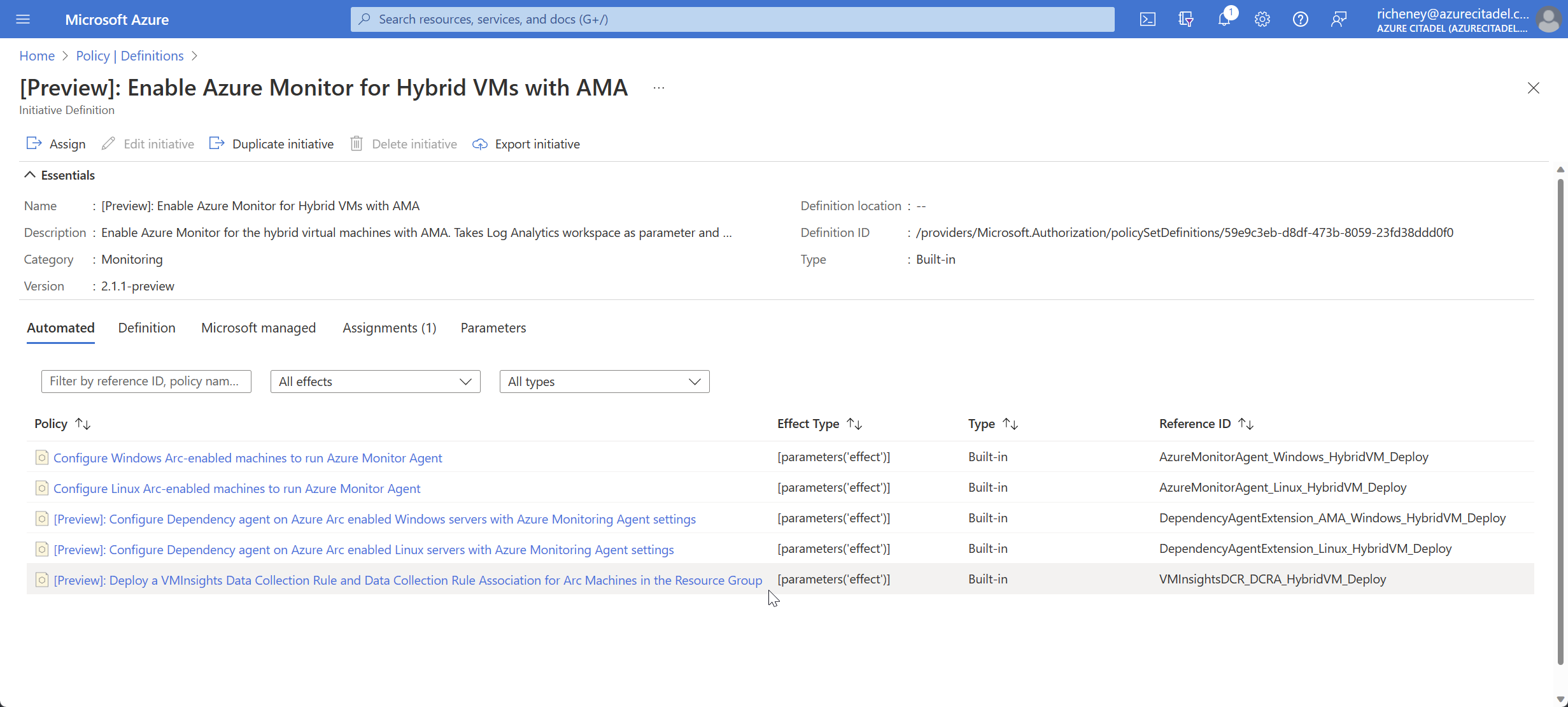
If you dive into the Dependency agent policies then you’ll notice that the extension deployment has a setting,
"enableAMA": "true", to configure it for the AMA rather than MMA. -
Check the parameters
The only required parameter value is logAnalyticsWorkspace.
The dataCollectionRuleName parameter value will default to
ama-vmi-default.The definition will prefix the dataCollectionRuleName with
MSVMI-and suffix it with-dcr, so the default DCR name will beMSVMI-ama-vmi-default-dcr.The enableProcessesAndDependencies boolean defaults to false.
⚠️ Don’t deploy the policy initiative via the portal even though that would be quicker.
We want to know how to automate this so will step through the process as an example.
Log Analytics workspace
When you looked at the policy initiative, the only required parameter values was a workspace ID.
Create a workspace in the arc_pilot resource group.
Name it MSVMI-ama-vmi-default-workspace to be consistent with the default DCR naming.
-
Create a Log Analytics workspace for VM Insights
az monitor log-analytics workspace create --name MSVMI-ama-vmi-default-workspace \ --resource-group arc_pilot --location westeurope
Required roles
The policies in the initiative use Deploy If Not Exists to provision the DCR, the AMA and Dependency extensions, and the DCR VM association.
You need to determine the required permissions for the managed identity if you are going to automate the deployment.
Return to the policy definition view and we’ll do a partial deployment to view the roles.
-
Click on Assign
-
Basics tab: Select the Landing Zones (alz-landingzones) management group
-
Parameters tab: Use the ellipsis (…) to select the subscription and workspace
-
Remediation tab: Check the permissions for the RBAC roles
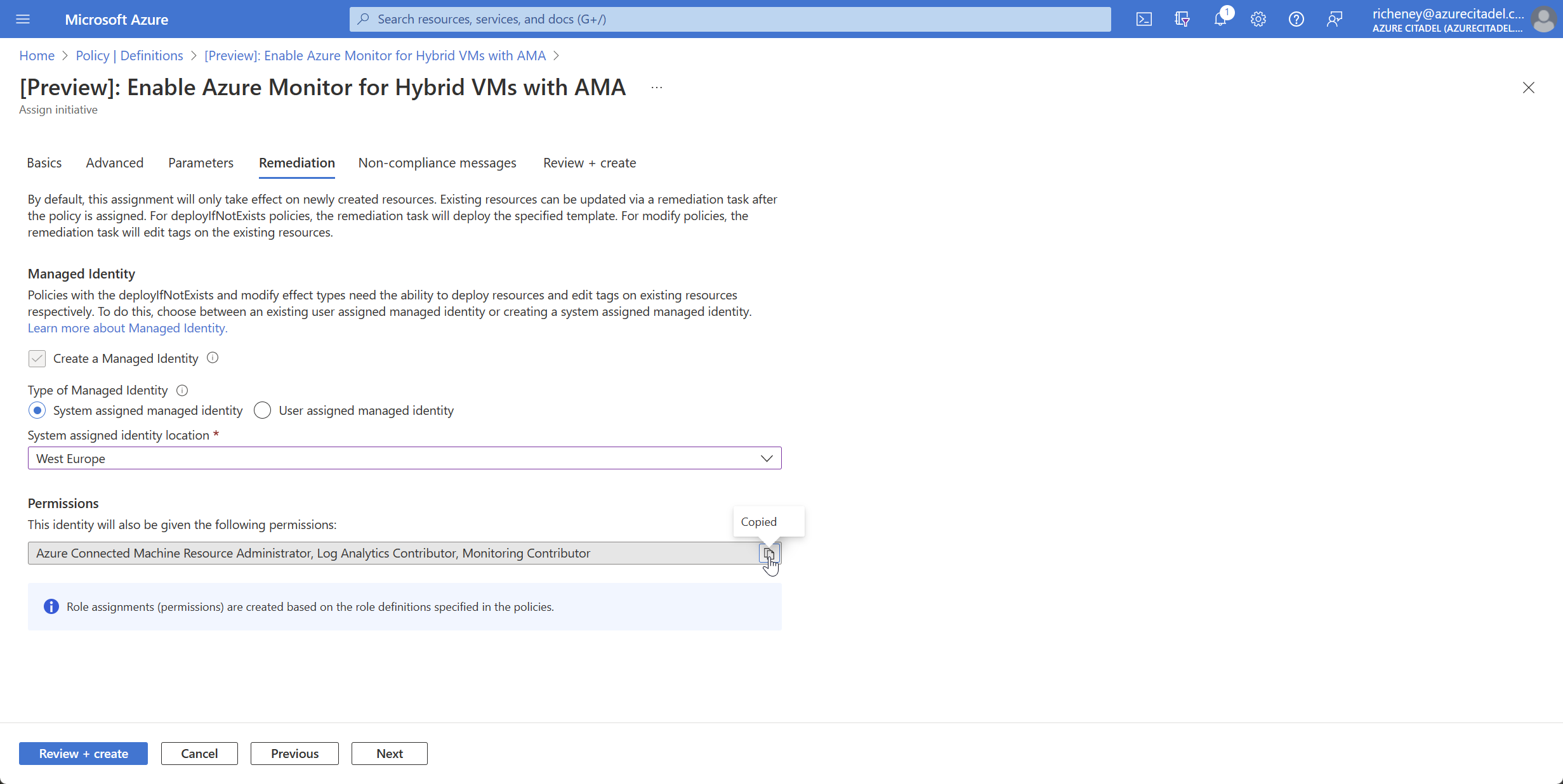
The required roles are:
- Azure Connected Machine Resource Administrator
- Log Analytics Contributor
- Monitoring Contributor
-
Click on Cancel
⚠️ Do not click on Create! You’ll assign the policy via the CLI.
Assign the policy
-
Get to the workspace ID
workspace_id=$(az monitor log-analytics workspace show --name MSVMI-ama-vmi-default-workspace \ --resource-group arc_pilot --query id --output tsv) -
Set scope to the Landing Zones management group
scope=/providers/Microsoft.Management/managementGroups/alz-landingzones -
Assign the policy initiative
az policy assignment create --name AMAhybrid \ --display-name "Enable Azure Monitor for Hybrid VMs with AMA" \ --description "Enable Azure Monitor for Hybrid VMs with Azure Monitor Agent (VM Insights)" \ --policy-set-definition 59e9c3eb-d8df-473b-8059-23fd38ddd0f0 \ --scope $scope \ --mi-system-assigned --location westeurope \ --identity-scope $scope \ --role "Azure Connected Machine Resource Administrator" \ --params "{\"logAnalyticsWorkspace\": {\"value\":\"$workspace_id\"}, \"enableProcessesAndDependencies\": {\"value\": true}}"Setting the enableProcessesAndDependencies boolean to true installs the Dependency agent.
The policies automatically set the agent’s enableAMA property to true.
You can only assign a single role when creating policy assignments via the Azure CLI.
-
Assign additional roles to the managed identity
az policy assignment identity assign --name AMAhybrid \ --scope $scope \ --system-assigned --identity-scope $scope \ --role "Log Analytics Contributor"az policy assignment identity assign --name AMAhybrid \ --scope $scope \ --system-assigned --identity-scope $scope \ --role "Monitoring Contributor"
Check the roles
-
Portal:
Filter on “Monitor” in Policy | Assignments, select Enable Azure Monitor for Hybrid VMs with AMA and select the Managed Identity tab.
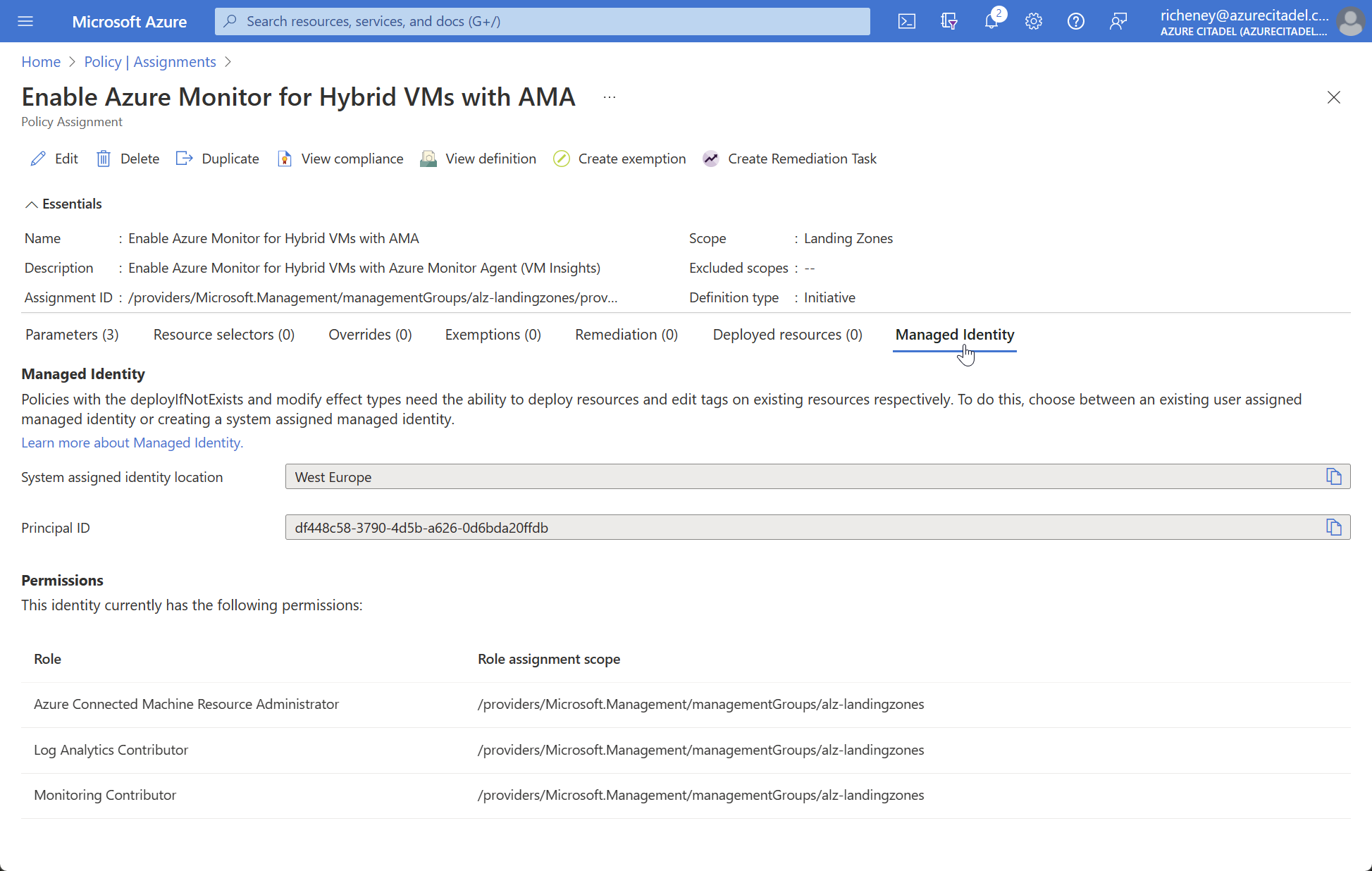
-
CLI:
identity_id=$(az policy assignment identity show --name AMAhybrid --scope $scope --query principalId --output tsv) az role assignment list --scope $scope --assignee $identity_id --query "[].roleDefinitionName"Expected output:
[ "Azure Connected Machine Resource Administrator", "Log Analytics Contributor", "Monitoring Contributor" ]
Success criteria
Show the proctor:
- the resource group name, location, tags and resources
- the RBAC assignment for Azure Arc Admins
- your tag inheritance policy assignments
- your VM Insights initiative assignment
- that the initial Enable Azure Monitor assignments have been deleted
Resources
- https://learn.microsoft.com/azure/azure-monitor/agents/agents-overview
- https://learn.microsoft.com/azure/azure-monitor/agents/azure-monitor-agent-migration
- https://learn.microsoft.com/azure/azure-monitor/vm/vminsights-overview
- https://learn.microsoft.com/azure/azure-monitor/vm/vminsights-enable-overview#agents
Next
The policy initiative is a great way to deploy the new Azure Monitoring Agent at scale, and you can also
In the next lab you will assign more policy initiatives for deploying additional extensions to hybrid machines.