Example
There is no 100% right answer to the scenario, but here is an example solution.
Table of Contents
Introduction
There are a number of requirements in the Azure Barista’s scenario that force you to deviate a little from the default management group structure, as defined by Azure Landing Zones. You will also need to create some additional custom policies to meet the customer’s specific needs. This is a very common thing to do after you have run through a design workshop.
On this page we will run through an example structure and explain the reasons why these decisions have been made.
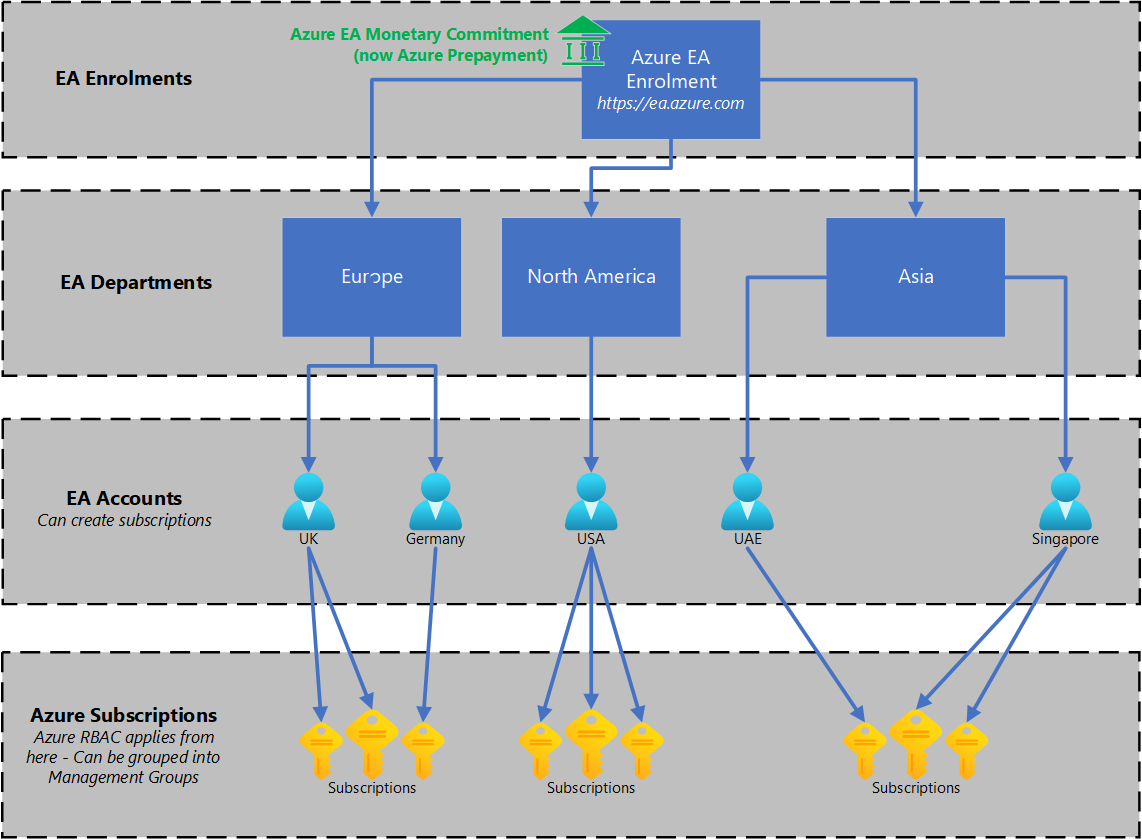
EA enrolment and AAD tenants
The EA Structure should look similar to the below:
Identity and access management
- The existing Azure AD Tenant of:
azurebaristas.onmicrosoft.comwill be used as:- Already synced with the On-Premise Active Directory Domain:
azbaristas.localvia Azure AD Connect with Password Hash Sync & SSO configured - Used already for Office/Microsoft 365 services across the organisation
- Already synced with the On-Premise Active Directory Domain:
- A single Azure AD Tenant is recommended as part of Azure Landing Zones & CAF Security best practices
- Relevant RBAC role/custom roles defined and applied as per RBAC requirements on the Day 2 Challenge Page & Day 1 Azure Baristas Intro
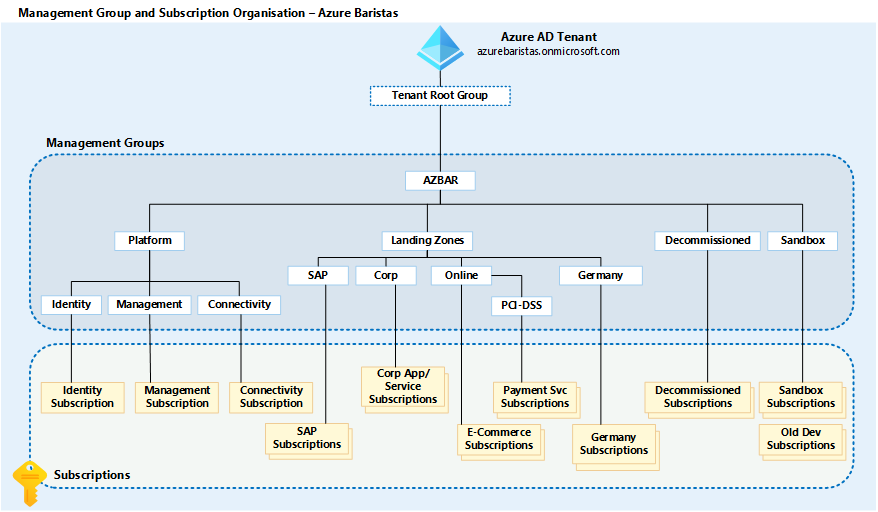
Management Group Structure
The Management Group structure should look similar to the below example:
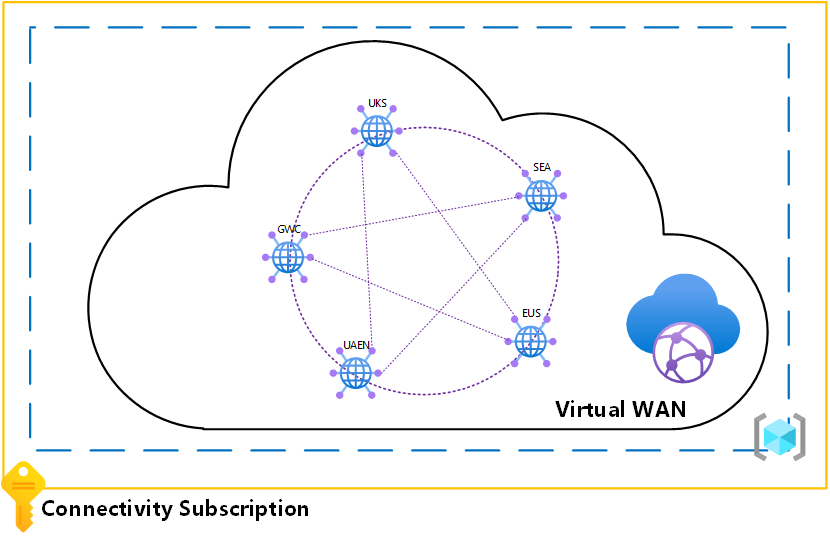
Network topology
- Azure Virtual WAN should have been chosen as the networking technology
- Due to the desire for moving towards SD-WAN
- Also Citrix skills within the networking team and Citrix being an Azure Virtual WAN partner
- Due to the desire for moving towards SD-WAN
- Also due to a lot of branch sites (Coffee Shops) required and the flexibility and speed Azure Virtual WAN will give Azure Baristas
- A Azure Virtual WAN Hub per Azure Region to be deployed in the Connectivity Subscription in a single Resource Group:
- UK South
- South East Asia
- Germany West Central
- UAE North
- East US
Management and monitoring
- All logs will be sent to a single Log Analytics Workspace deployed in the Management Subscription
Business continuity and disaster recovery
- Azure Policies (whether built-in, custom, or imported from Azure Landing Zone) in place as per backup requirements listed on the Day 2 Challenge Page & Day 1 Azure Baristas Intro
Security, governance and compliance
- Azure Policies (whether built-in, custom, or imported from Azure Landing Zone) in place as per all other requirements listed on the Day 2 Challenge Page & Day 1 Azure Baristas Intro
Platform automation and DevOps
Not currently in scope for the Azure Baristas scenario.
Source: https://www.azurecitadel.com/alz/day2/example/
Printed: